Investigating Outbound Connections
upgradeapi.PySimpleGUI.com Is Malware?
Alert
You get the following alert with 3 correlating events, is it a valid threat?
| Event Name | command_line | computer_name | process_path | md5 | IP | Port | Domain |
|---|---|---|---|---|---|---|---|
| EDR known malware | C:\Users\user01\Downloads\QuackMod_Windows\QuackMod.exe | sharedhost01 | C:\Users\user01\Downloads\QuackMod_Windows\QuackMod.exe | 8402c65c2f1aeb6e797911f653e6b7e0 | |||
| Outbound Network Connection | C:\Users\user01\Downloads\QuackMod_Windows\QuackMod.exe | sharedhost01 | C:\Users\user01\Downloads\QuackMod_Windows\QuackMod.exe | 8402c65c2f1aeb6e797911f653e6b7e0 | 143.42.125.232 | 5353 | upgradeapi.PySimpleGUI.com |
| CMD.exe Usage | C:\WINDOWS\system32\cmd.exe /c “ver” | sharedhost01 | C:\Users\user01\Downloads\QuackMod_Windows\QuackMod.exe | 8402c65c2f1aeb6e797911f653e6b7e0 |
How would you investigate this?
Hash Lookup
The binary has a md5 value of 8402c65c2f1aeb6e797911f653e6b7e0 , lets use VirusTotal to check the reputation.
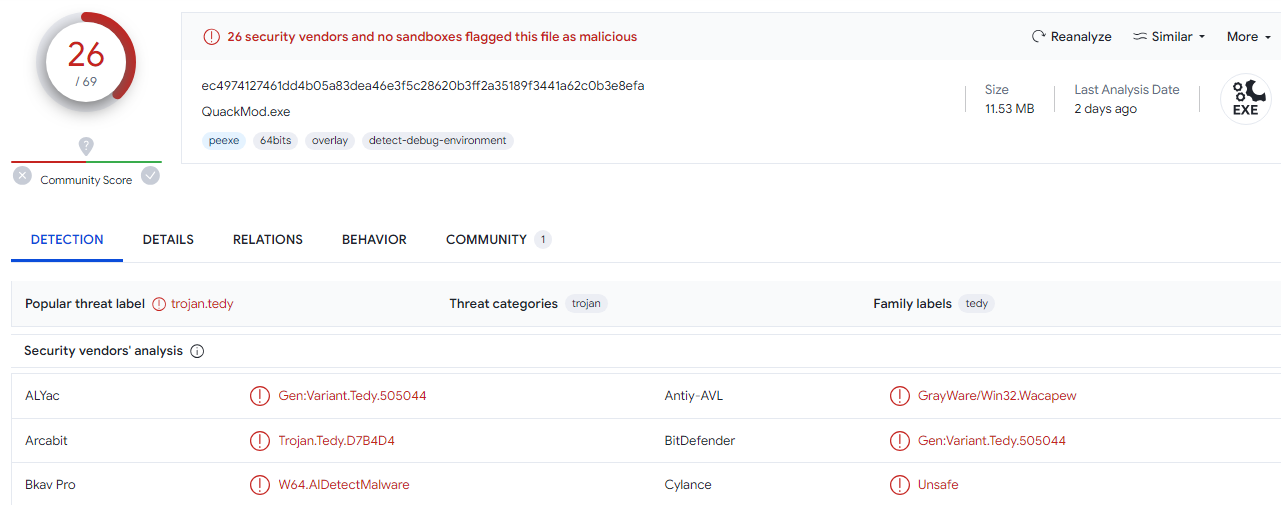
Yep, looks bad.
Outbound Network Connection
Let’s review the network connection made to upgradeapi.PySimpleGUI.com .
I already recognized the domain name PySimpleGUI shares the same name as the Python module https://pypi.org/project/PySimpleGUI/.
Resolving PySimpleGUI.com redirects you to their Github page https://github.com/PySimpleGUI/PySimpleGUI.
Malware making a network connection to PySimpleGUI.com would be very unusual, unless an attacker was able to compromise PySimpleGUI and setup a malicious service to upgradeapi.PySimpleGUI.com .
The port number 5353 is also interesting. 53 anything usually relates to DNS, but I doubt that in this case. Lets use Wannabrowser to examine what is potential running at upgradeapi.PySimpleGUI.com:5353 .
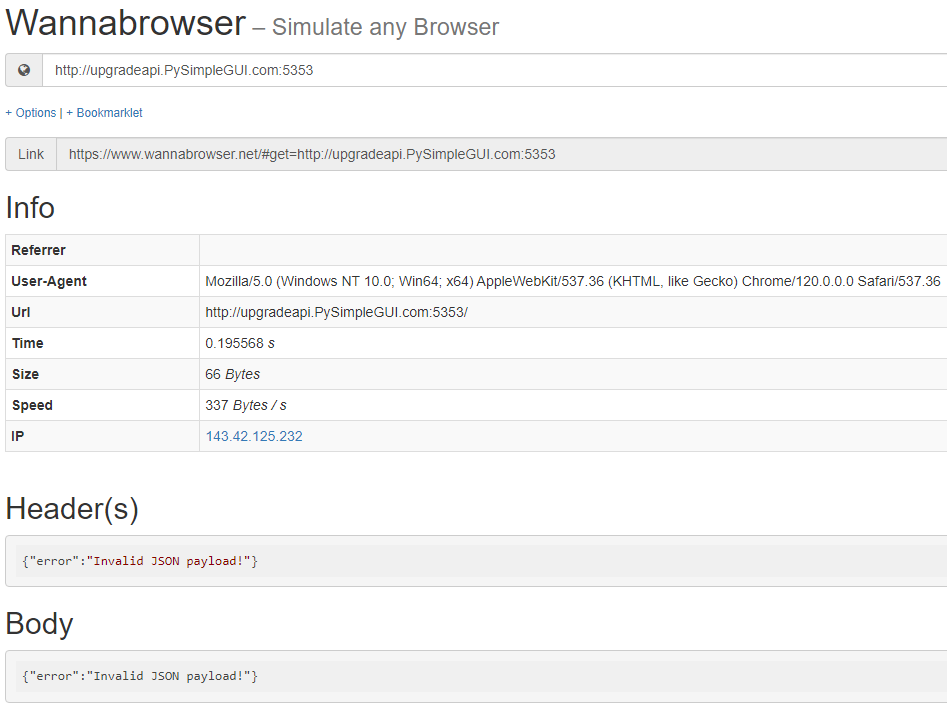
The service is expecting a json payload! This means the service is most likely collecting data through a POST request. The subdomain upgradeapi would make a great cover to masquerade anything malicious.
CMD.exe Usage
QuackMod.exe does spawn cmd.exe but it’s nothing special:
C:\WINDOWS\system32\cmd.exe /c "ver"
The only information returned from this command is the Windows OS version.
Google Search
VirusTotal and other hash reputation lookup services all seem to think this is malware, but so far I haven’t observed anything malicious yet. Let’s do a Google search to maybe find any new information about the domain upgradeapi.PySimpleGUI.com .
The very first result is a Github issue from PySimpleGUI that explains everything.
PySimpleGUI - Intelligent Upgrade Service
On April 26, 2023 PySimpleGUI added a new feature to their module called the “Intelligent Upgrade Service”.
This service was announced on May 1, 2023 in issue#142.
The service was created to:
improve stability and user experience, we’ve developed an Intelligent Upgrade Service to inform users when there are releases of PySimpleGUI that fix a problem that may be unique to their combination of components.
The new code was added to file PySimpleGUI.py and is defined starting on line 23,210. The Intelligent Upgrade Service is then executed on line 25,106.
Every time you import PySimpleGUI , the Intelligent Upgrade Service is executed.
What Data is Collected?
From PySimpleGUI.py line 23,350 we can see the dict defined for data collection:
upgrade_dict = {
'OSName' : str(os_name),
'OSVersion' : str(os_ver),
'PythonVersion' : str(python_ver),
'PSGVersion' : str(psg_ver),
'FrameworkName' : 'tkinter',
'FrameworkVersion' : str(framework_ver),
}
After reviewing the code for the service, I realized the service doesn’t use a POST request. The python code just uses the socket module to create a socket and connect to the server. We can just use WireShark to examine the packet ourselves.
I installed and imported PySimpleGUI into python and as expected the connection was captured.
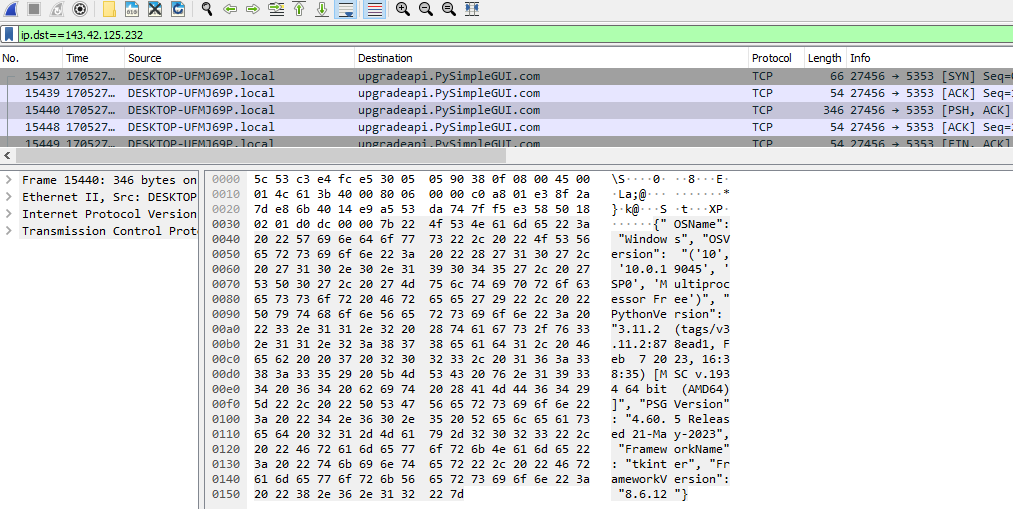
Now we can see the upgrade_dict in all it’s glory:
{"OSName": "Windows",
"OSVersion": "('10', '10.0.19045', 'SP0', 'Multiprocessor Free')",
"PythonVersion": "3.11.2 (tags/v3.11.2:878ead1, Feb 7 2023, 16:38:35) [MSC v.1934 64 bit (AMD64)]",
"PSGVersion": "4.60.5 Released 21-May-2023",
"FrameworkName": "tkinter",
"FrameworkVersion": "8.6.12"}
The Malware Classification Problem
VirusTotal, JoeSandBox, and Hybrid Analysis all classified this binary as malicious. All three have their own indicators for classifying this binary as malicious, but they all seem to agree that an outbound connection to upgradeapi.PySimpleGUI.com on port 5353 is suspicious.
Looking towards the bottom of PySimpleGUI’s Github issue#6567 gives an insight into what could be happening. Other developers are experiencing the issue of having their binary being declared malware from AV engines due to PySimpleGUI’s Intelligent Upgrade Service.
Developers turning their python project into a standalone exe that also uses PySimpleGUI are effected.
The only way to prevent the Intelligent Upgrade Service from execution is to rip out that part of the code from your project as there is currently no way to disable the service.